7 things you need to know about iOS 15.6 for iPhone, which includes over 35 security fixes

After nearly two months of beta testing, Apple is finally releasing the iOS 15.6 software update to all iPhone users. While it’s not as feature-rich as the iOS 15.5 or iOS 15.4 that came before it, there are still a few things you need to know about it.
The iOS 15.6 update, as well as iPadOS 15.6, were released to the masses on July 20 after five betas and two release candidates were provided to developers and public beta testers.
New controls for live sports in the TV app
There’s only one new feature that Apple is recognizing for iOS 15.6: a set of controls for live sports games in the TV app. With new controls, you can pause, rewind, or rewind live sports, and restart the entire broadcast to watch the game from the beginning.
Error correction
Other than the new TV controls for live sports gaming, the only thing Apple is acknowledging for iOS 15.6 are some bug fixes:
• Fixes an issue that could cause Settings to continue showing that the device’s memory is full even though it is available.
• Fixes an issue that could cause Braille devices to become slow or unresponsive when navigating through text in Mail.
• Fixes an issue in Safari that could cause a tab to return to the previous page.
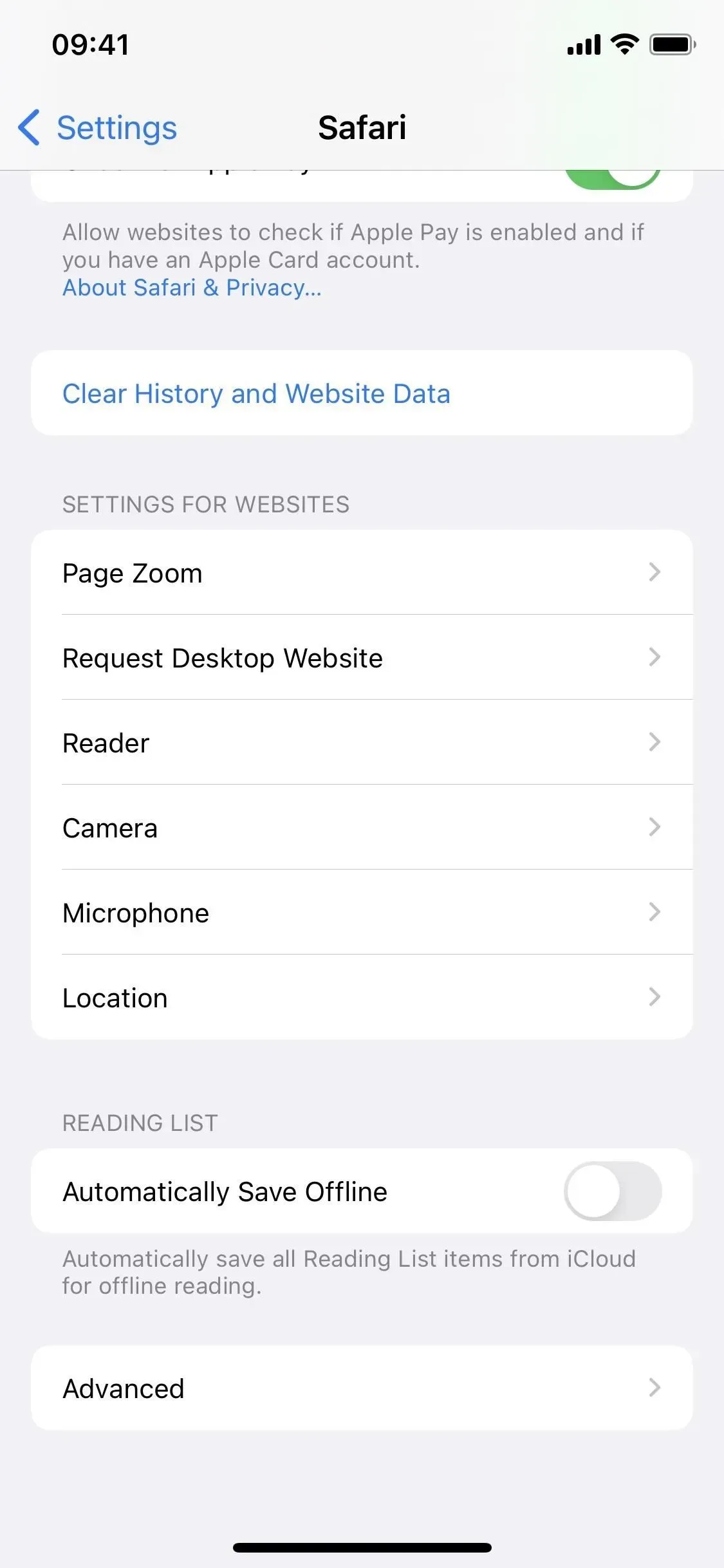
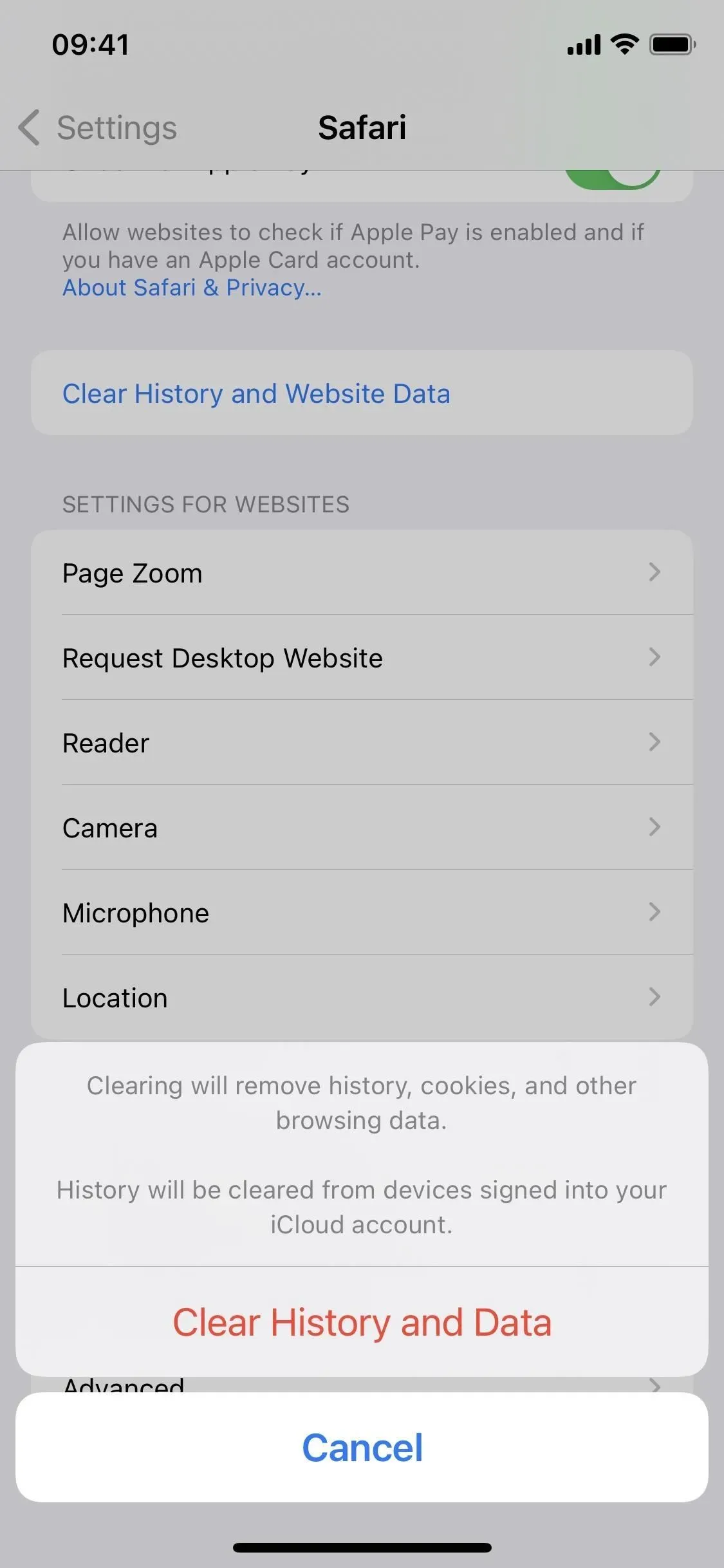
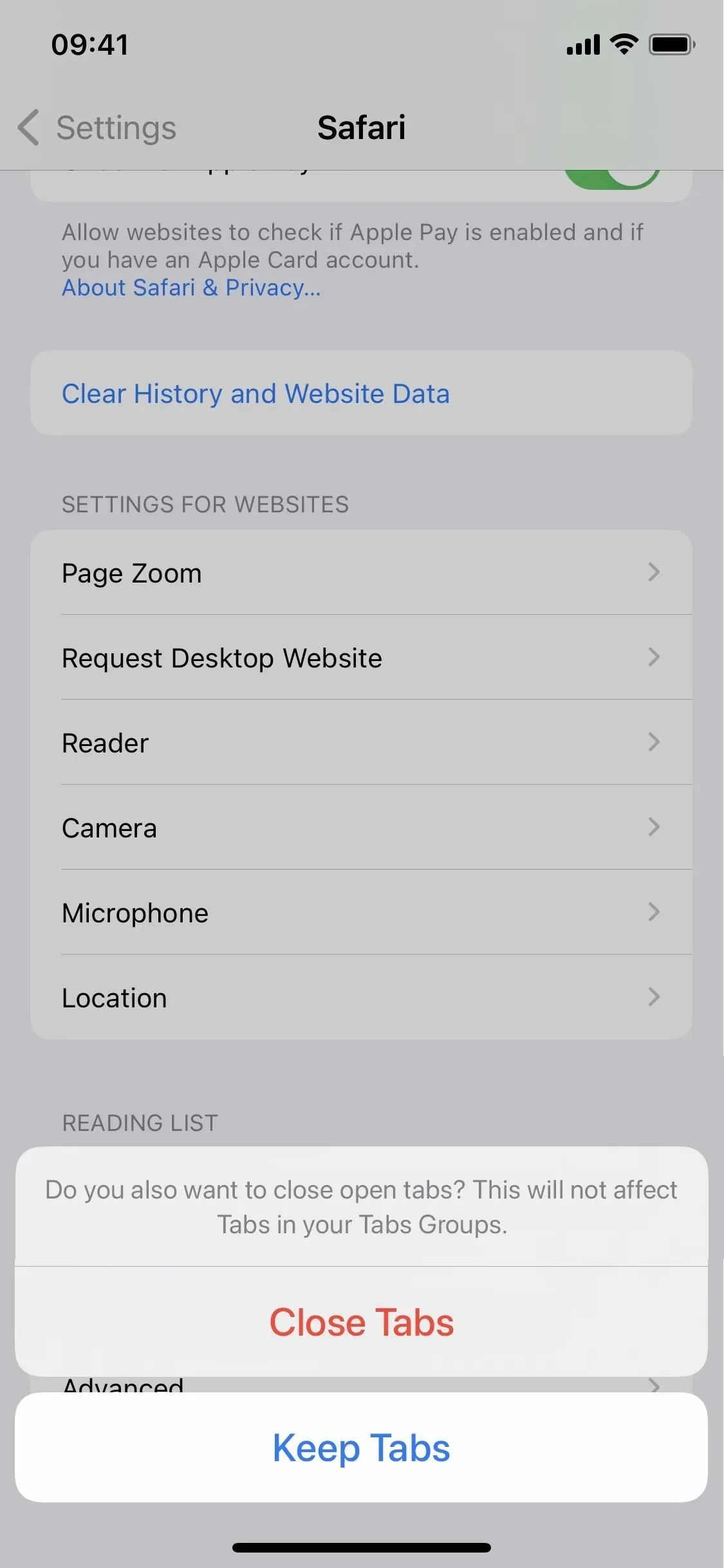
Clear tabs when clearing Safari data
Usually, when you go to Settings -> Safari -> Clear Website History & Data -> Clear History & Data, your history, cookies, and other browsing data will immediately disappear. In iOS 15.6, you may also be asked to “Close Tabs”or “Keep Tabs”. This setting is only for all of your open tabs in the main “[#] tab group”, but it won’t affect custom tab groups.
Improving communication security
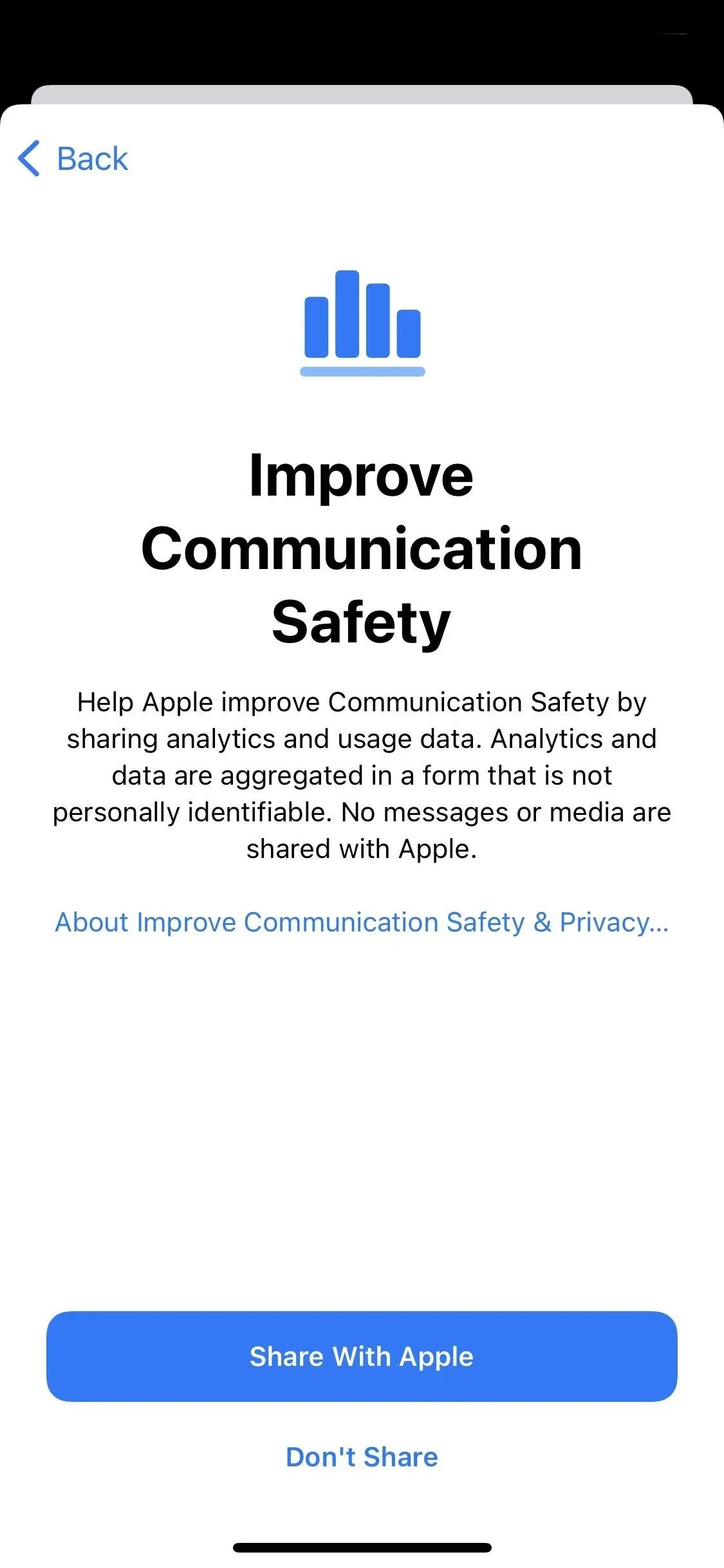
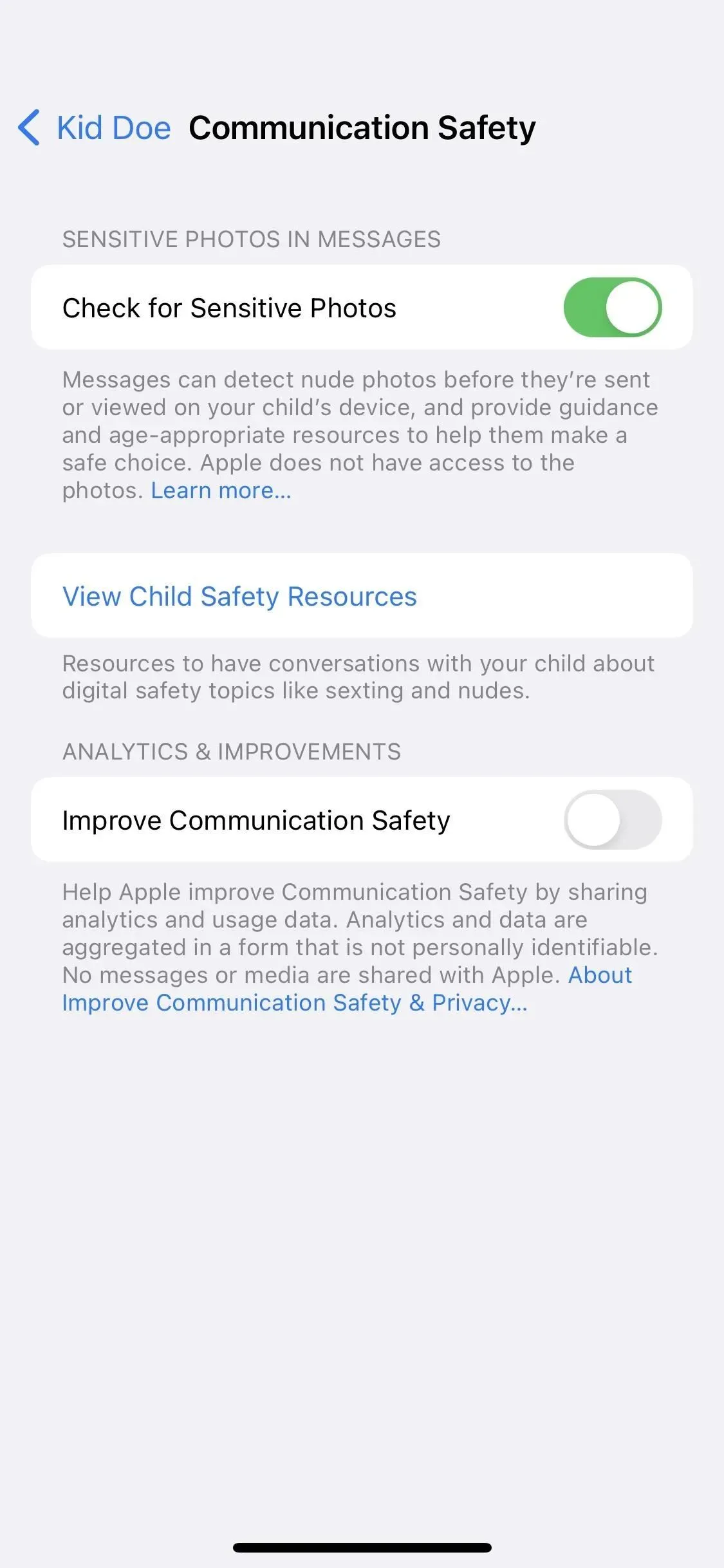
If you have a child in your family group, there is now an option in Settings -> Screen Time -> [Child Name] -> Communication Safety to “Enhance Communication Safety”. You can turn this switch on if you want to help Apple improve the Communications Security feature.
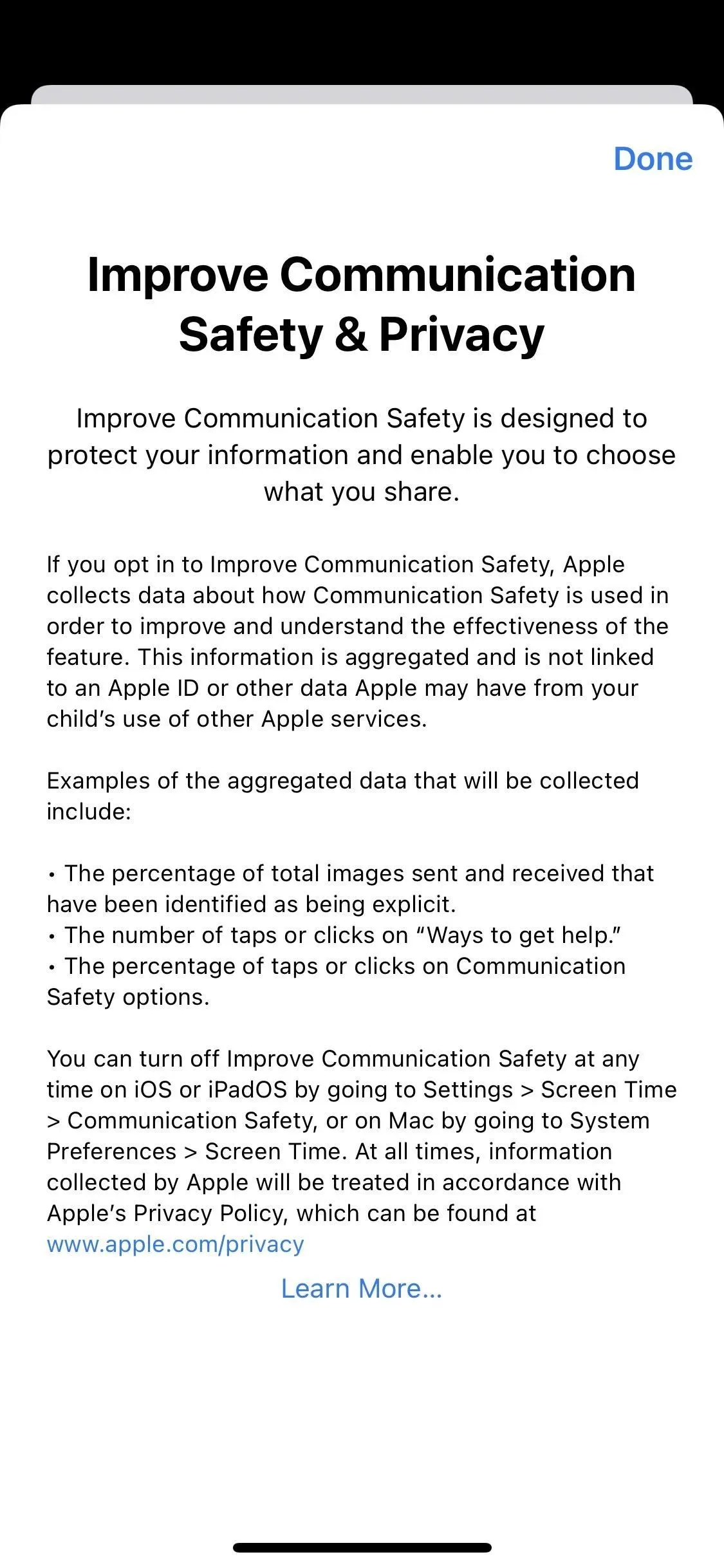
Help Apple improve communications security by sharing analytics and usage data. Analytics and data are collected in a form that does not allow for the identification of an individual. No messages or media are transmitted by Apple.
If you’ve never opened the Communication Security options, you may see a splash screen (left screenshot below) suggesting “Share with Apple”or “Don’t share”analytics and usage data. You may also see a notification on your child’s Screen Time page asking you to “Make your communications safer,”which opens the splash screen shown below.
New features for incoming international calls
Now, whenever you receive an international call from an unknown sender, iOS marks it as an international call and gives you the option to report it as unwanted.
Updated Home Invitation Menu
In the Home app, there is now a space between invitations to join homes, as shown below. Also, there are no “Accept”buttons in the home screen settings. Instead, you’ll see “View”which opens a screensaver with more information where you can accept or decline the invitation.
The most significant Home update to the invitation process is the new “Report Junk”button for invitations sent by unknown senders, i.e. users who are not in your contacts. Previously, you could simply accept or decline invitations from unknown contacts, but now you can view additional information or report it as spam.
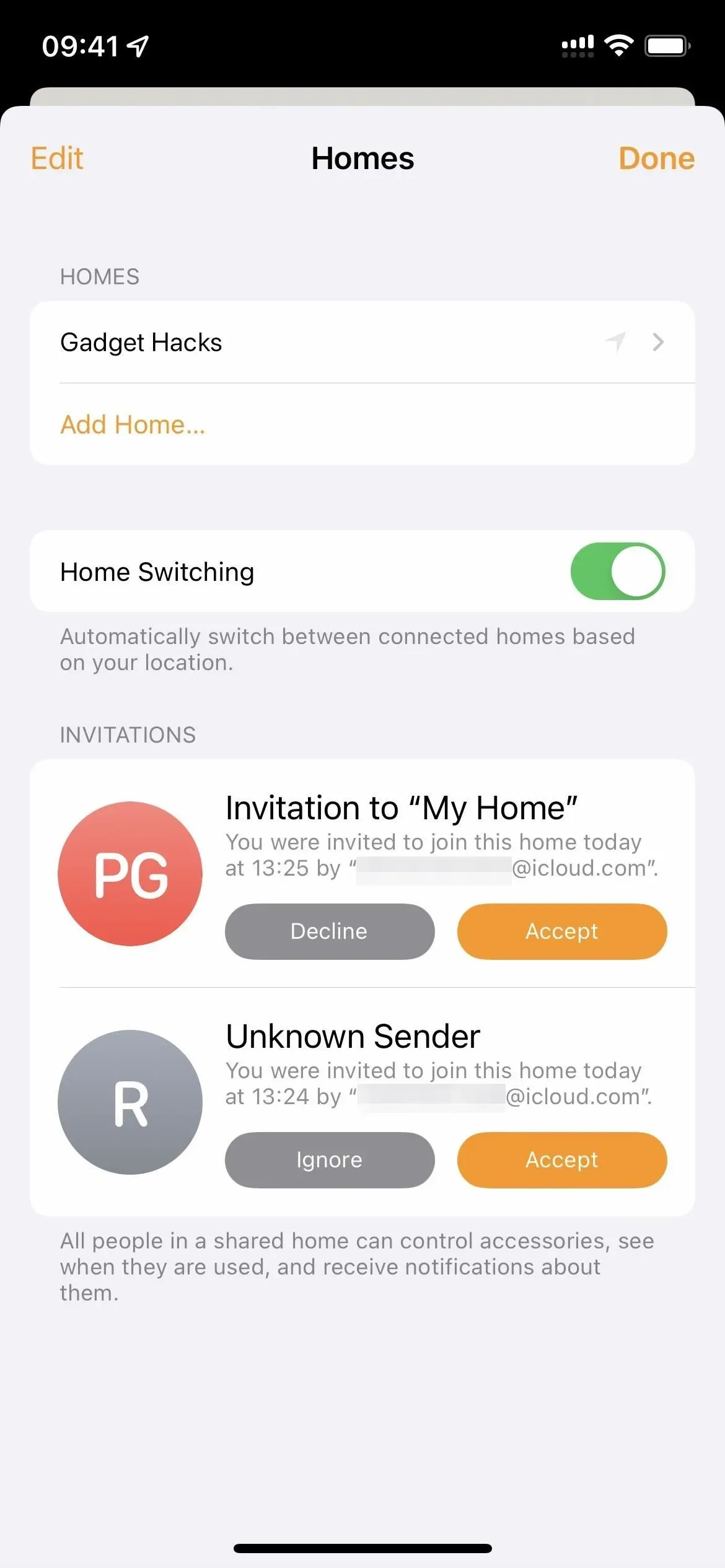
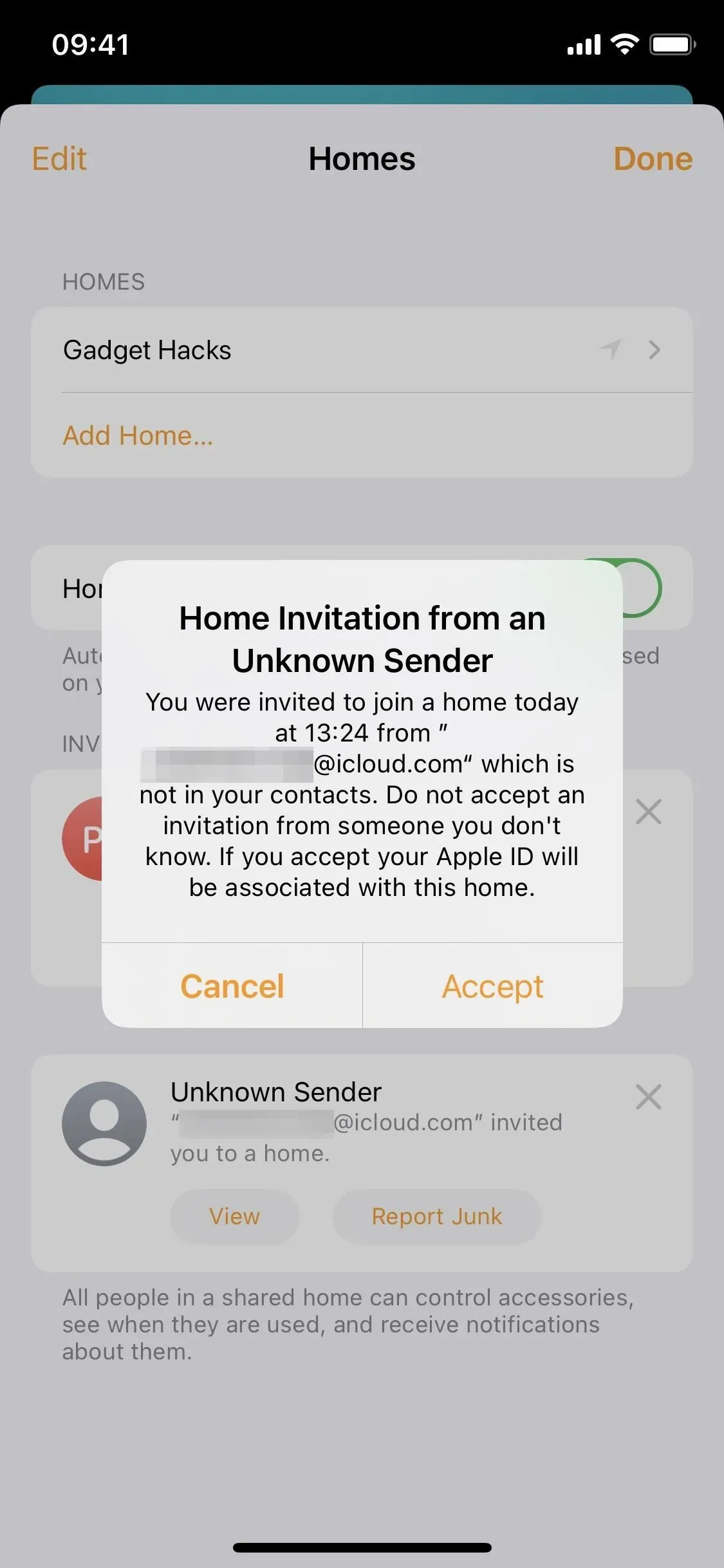
Home Settings in iOS 15.5 (left) and iOS 15.6 (right).
Over 35 security fixes
There are also 37 security updates, and some of the big ones fix vulnerabilities in Home, Safari Extensions, Wi-Fi, WebKit, WebRTC, and Kernel. There is even a vulnerability in a software update that allows “a user in a privileged position on the network to track the user’s activities. And another vulnerability for the iCloud Photo Library, where “the application can access the user’s sensitive information.”gives iOS 15.6 addresses:
- AFPS: An application with root privileges can execute arbitrary code with kernel privileges.
- AppleAVD: remote user can cause kernel code to be executed
- AppleAVD: Application can expose kernel memory
- AppleMobileFileIntegrity: App can get root privileges
- Apple Neural Engine: App may exit its sandbox
- Apple Neural Engine: Application can execute arbitrary code with kernel privileges
- Apple Neural Engine: Application can execute arbitrary code with kernel privileges
- Audio: An application can execute arbitrary code with kernel privileges.
- Audio: Application can expose kernel memory
- CoreMedia: App can expose core memory
- CoreText: A remote user may cause an unexpected application termination or arbitrary code execution.
- Filesystem events: An application can gain root privileges
- GPU drivers: application can expose kernel memory
- GPU drivers: An application can execute arbitrary code with kernel privileges.
- Home: The user can view restricted content from the lock screen.
- iCloud Photo Library: App can access user’s sensitive information
- ICU: Processing Malicious Web Content May Lead to Arbitrary Code Execution
- ImageIO: Malicious Image Processing May Expose Process Memory
- ImageIO: Processing a Malicious File May Lead to Arbitrary Code Execution
- ImageIO: Malicious Image Processing May Expose User Information
- ImageIO: image processing can lead to denial of service
- IOMobileFrameBuffer: An application can execute arbitrary code with kernel privileges.
- Kernel: An application with root privileges can execute arbitrary code with kernel privileges.
- Kernel: An application can expose kernel memory.
- Kernel: An application with arbitrary kernel read and write capabilities can bypass pointer authentication.
- Kernel: An application with arbitrary kernel read and write capabilities can bypass pointer authentication.
- Liblouis: An application may cause an unexpected application termination or arbitrary code execution
- libxml2: An application can pass sensitive user information.
- Multi-Touch: An application can execute arbitrary code with kernel privileges.
- PluginKit: application can read arbitrary files
- Safari Extensions: Visiting a Malicious Website Can Leak Sensitive Data
- Software update: A user with a privileged network position can monitor the user’s activities.
- WebKit: Visiting a website with malicious content can lead to UI spoofing.
- WebKit: Malicious Web Content Processing May Lead to Arbitrary Code Execution
- WebRTC: Malicious Web Content Processing May Lead to Arbitrary Code Execution
- Wi-Fi: The application may cause an unexpected system shutdown or write to kernel memory.
- Wi-Fi: A remote user may cause an unexpected system shutdown or kernel memory corruption.
Have you seen any new features in iOS 15.6? Let us know in the comments below!
Leave a Reply