A new fork of the Santander file manager adds partial support for viewing and modifying the contents of /var.
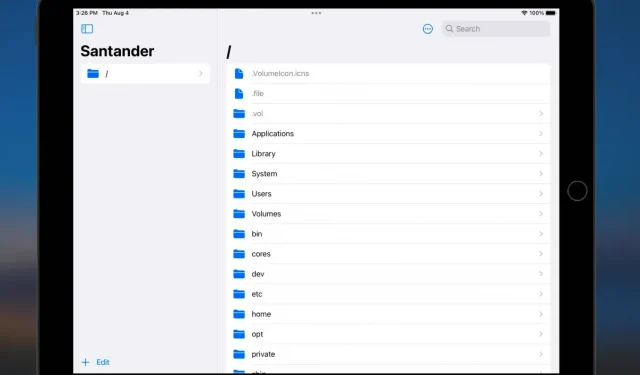
In early 2023, we showed you a MacDirtyCow-based file manager project called Santander that will allow you to view and make changes to the file system of your iOS or iPadOS 15.x-16.1.2 device without jailbreak.
Santander was originally created by @CoreSerena, and while the version of SantanderMacDirtyCow we showed you earlier this year was forked by palera1n team member @mineekdev, there is now another fork available on GitHub called SantanderEscaped @haxi0sm that appears to support making changes to files in /var.
Referring to a post posted to /r/jailbreak early Saturday morning, SantanderEscaped allows users to access and modify files in /var, but not completely, as there are several restrictions in @zhuowei’s tccd exploit that prevent extravagant changes. In particular, the exploit does not change the permissions of some folders located in /var, which will be required to make these changes.
So while most of the content found in /var will be both readable and writable in the new build of SantanderEscaped, a smaller amount of content will not be, such as app containers, as pointed out by iOS developer Evangelista in a comment in message /r/jailbreak. This limits what users can do in certain folders.
While this is a baby step, it is a step in the right direction. With a simple exploit, the SantanderEscaped project allows you to modify more files than the version we showed earlier this year and does not require a jailbreak. Instead, it continues to rely on the MacDirtyCow exploit for iOS and iPadOS 15.x-16.1.2 devices, no matter what chip is inside.
If you’re interested in learning more about the SantanderEscaped project, you can view it on GitHub. Please note that the project is still in beta, so bugs may be present.
Do you plan to take advantage of the updated Santander file manager now that it can access certain parts of /var? Let us know in the comments section below.
Leave a Reply