Social Media Safety Tools & Risk Mitigation Tips [2023]
![Social Media Safety Tools & Risk Mitigation Tips [2023]](https://cdn.4pmtech.com/wp-content/uploads/2023/07/social-media-security-3-640x375.webp)
Social media security may not be the most exciting part of your social marketing strategy. But it may be the part that saves your business from a critical security breach or major business loss.
Whether you’re a one-person store or an organization with a large social team, you need to understand how best to mitigate the risks associated with social media so you can better focus on earning rewards.
Social media security refers to strategies that businesses and individuals can use to protect their social media accounts from threats such as hacking, phishing, and malware.
In this section, we’ll look at:
- Phishing attacks and scams
- Self-proclaimed accounts
- Malicious attacks and hacks
- Vulnerable Third Party Applications
- Password theft
- Privacy settings and data security
- Unsecured mobile devices
Phishing attacks and scams
Phishing scams are among the most common cybersecurity threats on social media. The purpose of phishing is to trick you or your employees into handing over passwords, banking details, or other sensitive information.
One common phishing scam involves fake coupons for well-known brands such as Costco, Starbucks, and Bath & Body Works. This is especially popular on Facebook. To receive a coupon, you must provide personal information such as your address and date of birth.
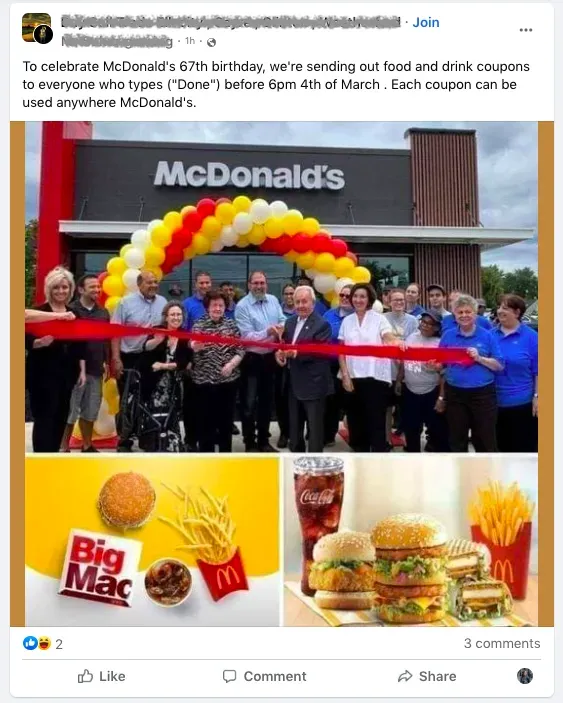
Source: Facebook
Some scammers are more daring, asking for bank information and passwords for a coupon processing fee.
Romance scams are another common social media safety issue, with 40% of those who fall victim to this type of scam say it started on social media. For users aged 18 to 29, the FTC reports that sextorsion scams occurring on Instagram and Snapchat were of particular concern in 2022.
For Americans aged 20 to 39, social media is the most common way to contact scammers.
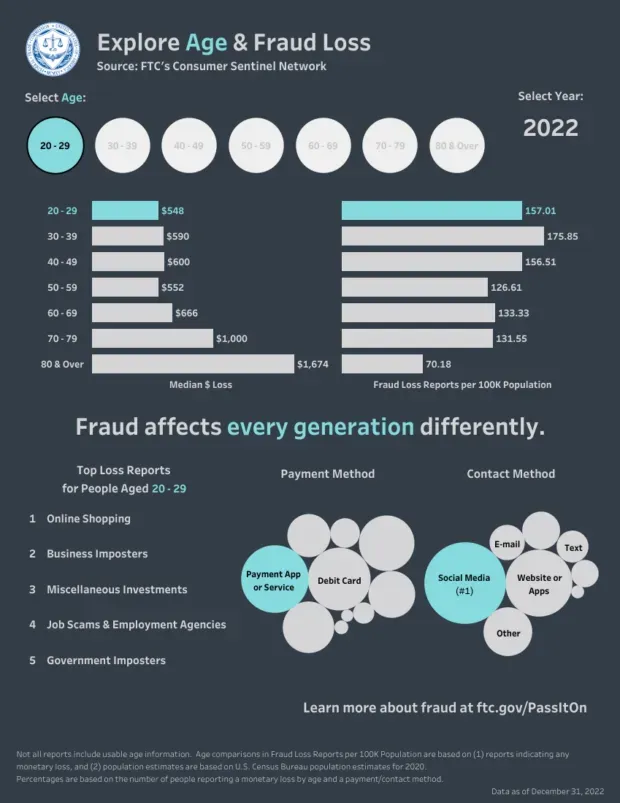
Source: Federal Trade Commission.
Self-proclaimed accounts
It is relatively easy for a scammer to create a social media account that looks like it belongs to your company. This is one of the reasons why social media verification is so important.
LinkedIn’s latest Transparency Report notes that they have taken action against 21.9 million fake accounts in just six months. Most of these accounts (95.3%) were automatically blocked upon registration. But more than 190,000 fake accounts were reviewed just after members reported them.
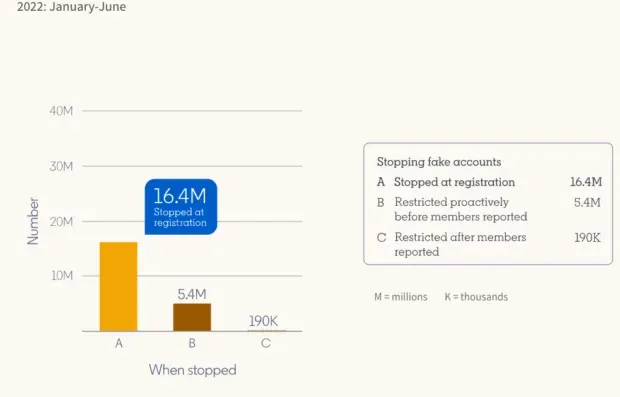
Source: LinkedIn community report.
Meanwhile, Facebook took action against 1.3 billion fake accounts between October and December 2022. The social media platform estimates that 4-5% of monthly active users are fake accounts.
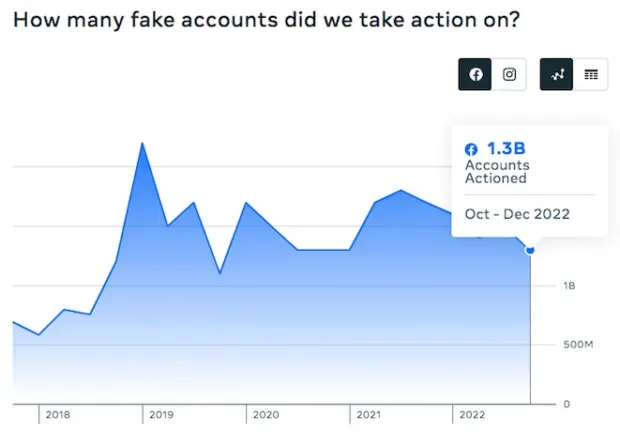
Source: Meta Community Compliance Report.
Imposter accounts can target your clients, employees, or potential employees. When your connections are tricked into giving away sensitive information, your reputation suffers. Imposter accounts can also try to force employees to hand over their login credentials to corporate systems.
Another type of impostor scam targets brands hoping to work with influencers. In this scam, someone posing as a social media personality with a large following reaches out and asks for a free product.
Working with real influencers can be a valuable marketing strategy. But it’s important to make sure you’re dealing with a real person.
Malicious attacks and hacks
In one of the most embarrassing recent cybersecurity incidents on social media, the personal Twitter account of the U.S. Ambassador-at-Large for Cyberspace and Digital Policy was hacked in February:
My account was hacked. Job hazards…
— Nate Fick (@ncfick) February 5, 2023
If hackers gain access to your social media accounts, they can cause massive damage to a brand’s reputation. If they manage to install malware, there is an even greater risk.
In 2022, the Ducktail campaign was discovered to target LinkedIn employees and then convince them to open an attachment containing malware. The malware used browser cookies to hijack the victim’s Facebook business accounts.
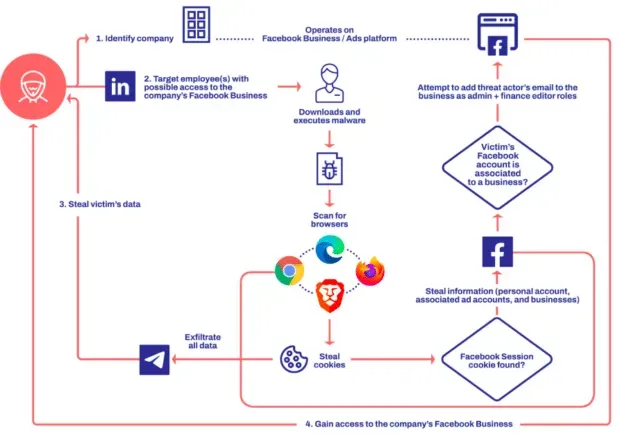
Source: WithSecure
Vulnerable Third Party Applications
Blocking your own social media accounts is great. But hackers can still access your secure social networks through vulnerabilities in connected third-party apps.
Instagram specifically warns about third-party apps that claim to provide likes or followers:
“If you give these apps your login information, whether it’s an access token or your username and password, they can get full access to your account. They can view your private messages, find information about your friends, and potentially post spam or other harmful content on your profile. It jeopardizes your safety and the safety of your friends.”
Password theft
Those social media quizzes that ask about your first car might seem like harmless fun. But online challenges and social media quizzes are a common method of gathering password information or retrieving personal data, often used as clues to a forgotten password.
By filling them out, employees may inadvertently create security issues on social media.
Don’t answer other online quiz questions until you’ve read this: https://t.co/AWI9p5UqcJ.
— FTC (@FTC) February 6, 2023
Privacy settings and data security
It appears that people are well aware of the potential privacy risks when using social media. General trust in social media’s ability to protect privacy and data has been declining in recent years. In particular, TikTok has been in the news recently as governments around the world restrict access to the platform on official hardware due to data security concerns.
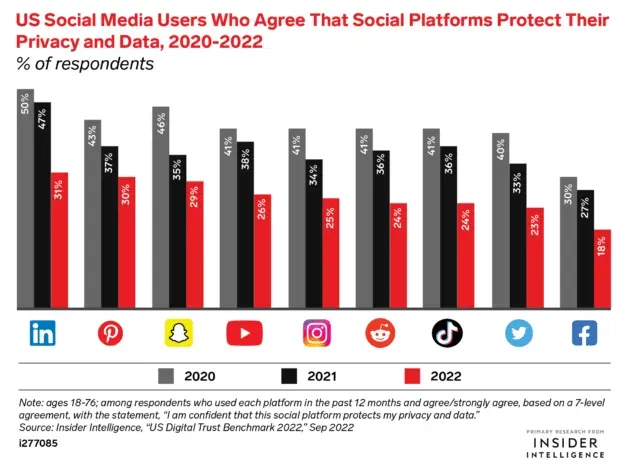
Source: eMarketer
These concerns, of course, do not prevent people from using their favorite social channels. The number of active social media users grew by 4.2% in 2022 to 4.74 billion people.
Make sure you and your team understand the privacy policy and settings for both your personal and business account. You must provide privacy guidance for employees who use their personal social accounts at work.
Unsecured mobile phones
Mobile devices account for more than half of the time we spend online. Social media apps make it easy to access your social media accounts with just one tap.
It’s great as long as your phone stays in your hands. But if your or an employee’s phone is lost or stolen, one-touch access makes it easy for a thief to access social accounts. They can then post to your account or even alert your contacts to phishing or malware attacks.
Protecting the device with a password, fingerprint, or face verification helps, but a surprising number of mobile users still leave their phones unlocked.
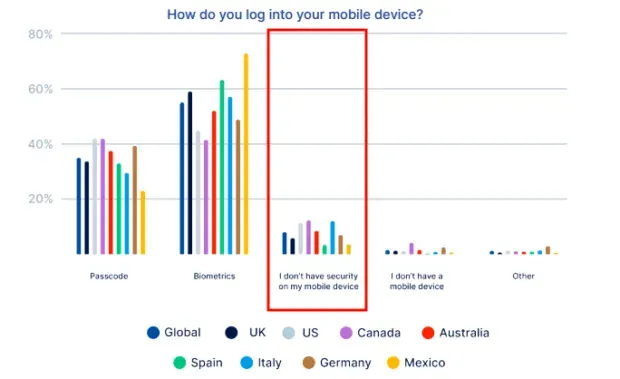
Source: iProov Digital Identity Report.
1. Create a social media policy
A social media policy is a set of guidelines that outlines how your business and your employees should use social media responsibly.
This will help protect you not only from social media and cybersecurity threats, but also from bad publicity or legal issues.
At a minimum, the security section of your social media policy should include:
- Rules for using personal social networks on business equipment
- Social media activities to avoid, such as quizzes that ask for personal information.
- Which departments or team members are responsible for each social media account
- A guide on how to create an effective password and how often to change passwords
- Expectations for continuous software and device updates
- How to identify and avoid scams, attacks and other security threats
- Who to notify and how to respond if a social media security issue arises
For more information, see our step-by-step guide to creating a social media policy. It includes many examples from different industries.
2. Require two-factor authentication
Two-factor authentication is not secure, but provides a powerful extra layer of security for your social media accounts. You don’t have to take our word for it how important this is,” Instagram CEO Adam Mosseri reminds his followers on a monthly basis.
Telephone? Check? You understand… ?
? Profile → Settings → Security → Two-factor authentication ? pic.twitter.com/DEaIClhYIb
— Adam Mosseri (@mosseri) March 1, 2023
3. Train your employees on social media safety
Even the best social media policy won’t protect your organization if your employees don’t follow it. Of course, your policy should be easy to understand. But training will give employees the opportunity to participate, ask questions, and understand the importance of following.
These training sessions also provide an opportunity to familiarize yourself with the latest social media threats. You can talk about whether there are any sections of the policy that need to be updated.
It’s not all doom and gloom. Social media training will also help your team use social tools effectively. When employees understand best practices, they feel confident using social media for their work. They are then well prepared to use social media safely for both personal and professional purposes.
4. Restrict Access to Improve Social Media Data Security
Restricting access to your social media accounts is the best way to keep them safe. You may be focused on threats from outside your organization. But employees are an important source of data breaches.
You might have entire teams of people working on social media messaging, post creation, or customer service. But this, of course, does not mean that everyone should know the passwords to your social media accounts.
It’s critical to have a system in place that allows you to revoke access to accounts when someone leaves your organization or changes roles. Learn more about how this works in the Tools section below.
5. Set up a social media post approval system
Not everyone who works with your social media accounts needs the ability to post. An important defensive strategy is to limit the number of people who can post on your accounts. Think carefully about who needs the publishing opportunity and why.
You can use Hootsuite to give employees or contractors the ability to draft messages. They are then all set to publish at the click of a button. Leave the last button press to a trusted person on your team.
6. Put someone in charge
Appointing a key person as the eyes and ears of your social presence can go a long way in reducing risk. This person must:
- own social media policy
- track your brand’s social media presence
- determine who has access to the publication
- be a key player in developing your social media marketing strategy
This person will most likely be a senior player on your marketing team. But they must maintain a good relationship with your company’s IT department to ensure that marketing and IT work together to mitigate risk.
This is the person that team members should turn to if they ever make a mistake on social media that could put the company at risk of any kind. Thus, the company can initiate an appropriate response.
7. Set up an early warning system with social media security monitoring tools.
Keep track of all your social channels. This includes the ones you use every day, as well as the ones you registered but never used.
Have someone check the legitimacy of all messages in your accounts. Cross-referencing your posts in the content calendar is a great place to start.
Watch out for the unexpected. Even if a post seems legitimate, it’s worth investigating if it deviates from your content plan. It could be simple human error. Or it could be a sign that someone has gained access to your accounts and is testing the water before posting something more malicious.
Use your social media monitoring plan to keep an eye on:
- self-proclaimed accounts
- inappropriate mentions of your brand by employees
- inappropriate mentions of your brand by anyone associated with the company
- negative conversations about your brand
You can learn how to keep track of all conversations and accounts related to your brand in our complete guide to social media listening. And check out the Tools section below for resources that can help.
8. Regularly check for new social media security issues.
Social media security threats are constantly changing. Hackers are always coming up with new strategies, and new scams and viruses can appear at any time.
Regular reviews of your social media security measures will help you stay ahead of intruders.
At least once a quarter, be sure to review:
- Social media privacy settings. Social media companies update their privacy settings regularly. This may affect your account. For example, a social network may update its privacy settings to give you finer control over how your data is used.
- Access and publishing rights. Check who has access to your social media management platform and social media accounts. Update as needed. Make sure all former employees have their access revoked. Check anyone who has changed roles and no longer needs the same level of access.
- Recent social media security threats. Maintain a good relationship with your company’s IT department to increase social media security awareness. They can inform you about any new social media security threats. And stay tuned – major hacks and new major threats will be reported by major news outlets.
- Your social media policy. This policy must evolve over time. As new networks gain popularity, security best practices change and new threats emerge. Reviewing it quarterly will ensure that this document remains useful and helps keep your social media accounts secure.
As closely as you monitor your social feeds, you can’t track them 24 hours a day, but the software can. Here are some of our favorite social media security tools.
1. Houtsuit
With a social media management platform like Hootsuite, team members never need to know the login details of any social media account. You can control access and permissions, so each person only gets the access they need.
If someone leaves the company, you can disable their account without changing all of your social media passwords.
Hootsuite is also an effective social monitoring tool that keeps you ahead of threats. By monitoring social media mentions of your brand and keywords, you will know immediately when suspicious conversations about your brand appear.
Let’s say people share fake coupons, or a fake account starts tweeting on your behalf. You will see this activity in your streams and be able to take action before your customers are scammed.
Hootsuite is also FedRamp authorized and Cyber Essentials compatible. Learn more about our risk management program and information security policies.
2. ZeroFOX
ZeroFOX is a cybersecurity platform that provides automatic alerts for:
- dangerous, threatening or offensive social content aimed at your brand
- malicious links posted on your social accounts
- fraud targeting your business and customers
- fraudulent accounts impersonating your brand
It also helps protect against hackers and phishing attacks.
3. BrandFort
BrandFort can help protect your social media accounts from spam, phishing comments, and other content moderation issues.
Why are spam comments a security risk? They are visible on your profiles and may encourage legitimate followers or employees to visit fraudulent sites. You will have to deal with the consequences even if you didn’t spam directly.
BrandFort can detect spam comments in multiple languages and hide them automatically.
Frequently Asked Questions About Social Media Security
What are the top 5 social media security threats?
Top 5 Social Media Security Threats:
- Phishing attacks and scams
- Self-proclaimed accounts
- Malicious attacks and hacks
- Vulnerable Third Party Applications
- Password theft
How do you keep social media safe?
The best way to improve your social media security is to limit account access and use two-factor authentication.
Leave a Reply