Security Researcher releases PoC with r/w core for Neural Engine devices running iOS 15 and macOS 12

Security researcher @_simo36 turned quite a few heads by posting a tweet on Friday that appears to contain a proof-of-concept (PoC) for an exploit chain called WeightBufs that provides kernel memory read and write capabilities in some versions of iOS and iPadOS 15 and macOS. 12.
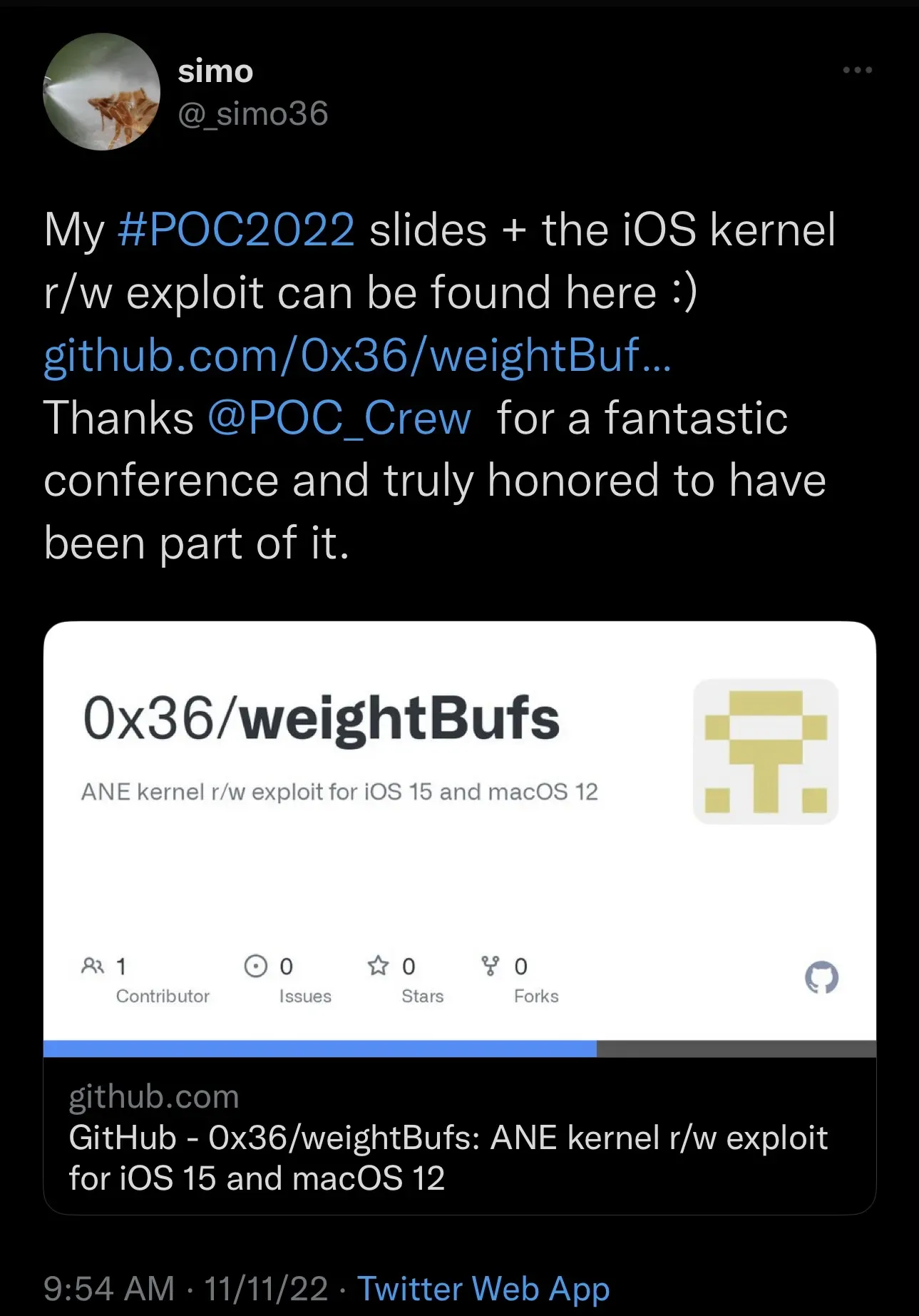
In the tweet, @_simo36 points to a GutHub page that contains not only all the information about the exploit, but also the slides for the presentation they gave at POC2022.
The exploit itself appears to support all versions of iOS and iPadOS 15 on Neural Engine devices (A11 and later), but does not support iOS and iPadOS 16; but iOS and iPadOS 15.6 fixes a sandbox escape that breaks the chain of exploits used to crack WeightBufs. With that in mind, the full exploit chain is currently only available for iOS and iPadOS 15.0-15.5 and macOS 12.0-12.4.
The above issue highlights one of the major issues affecting jailbreaks today, which is how methods have become more important than kernel exploits themselves. No kernel exploit will jailbreak current iOS or iPadOS firmware as Apple continues to harden iPhone and iPad security. Because of this, jailbreak developers need additional resources, such as bypasses and sandbox escapes, just to achieve this. The logic of navigation through all these mechanisms is the technique.
The @_simo36 exploit chain exploits at least four different vulnerabilities that have already been reported to Apple, including the following:
- CVE-2022-32845: Added signature verification bypass for model.hwx.
- CVE-2022-32948: DeCxt::FileIndexToWeight() Read OOB due to missing array index check.
- CVE-2022-42805: ZinComputeProgramUpdateMutables() random read possible due to integer overflow issue
- CVE-2022-32899: DeCxt::RasterizeScaleBiasData() Buffer underrun due to integer overflow issue.
@_simo36 currently says they have successfully tested their exploit chain on the following combinations of devices and firmware:
- iPhone 12 Pro (iPhone 13.3) running iOS 15.5
- iPad Pro (iPad 8,10) running iPadOS 15.5
- iPhone 11 Pro (iPhone 12.3) running iOS 15.4.1
- MacBook Air (10.1 with M1 chip) running macOS 12.4
So we know you’re all asking the burning question: “Can this be used to break out of jail?”And the simple answer to this question would be no, because this is only one piece of a larger puzzle, and much more work will be required to create a jailbreak and run it on end users’ devices.
However, the proof of concept is a great example of a masterful hack, and we can only hope it helps solve the puzzle faster as several hack teams work in the background to develop jailbreaks for iOS and iPadOS 15.
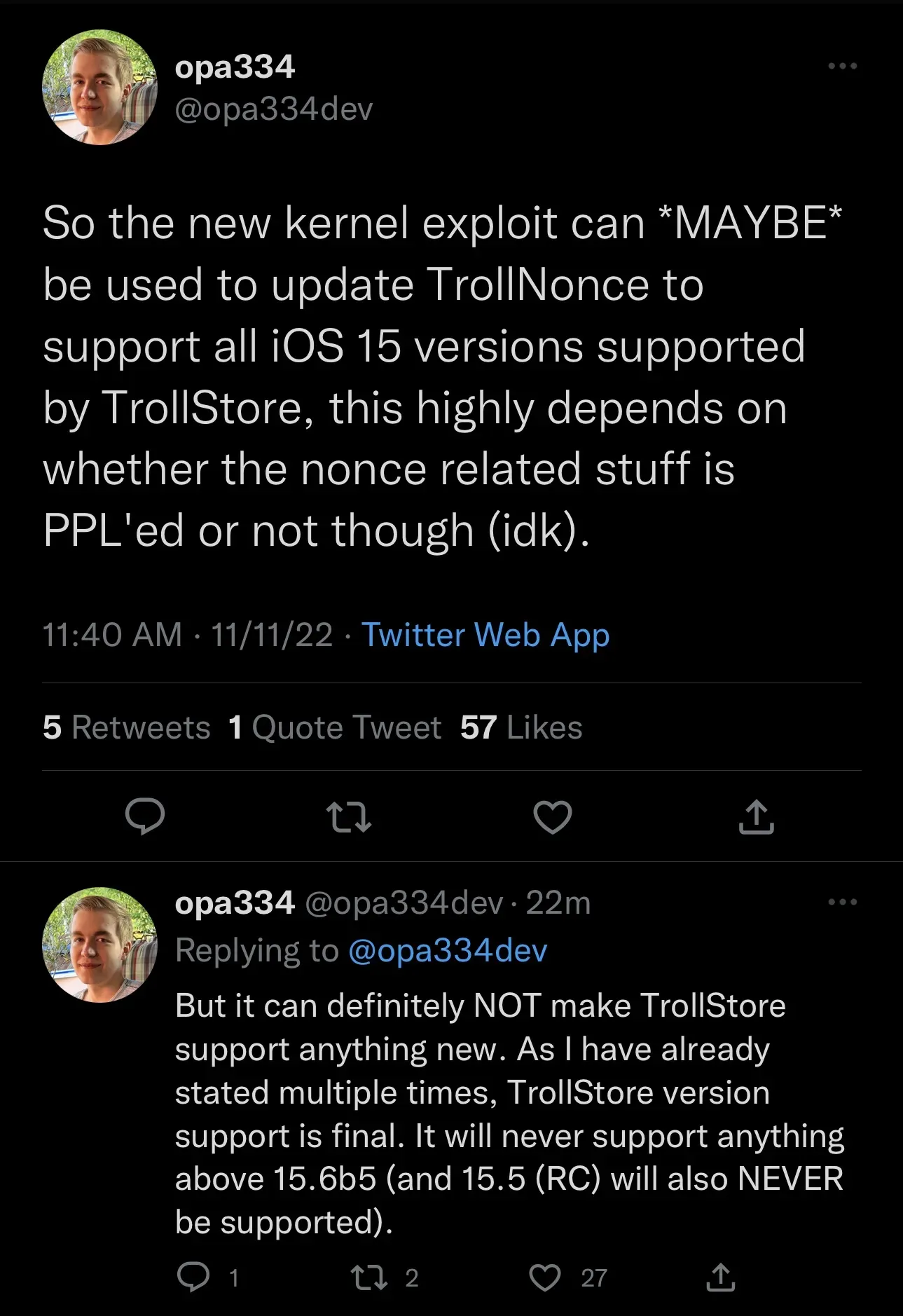
In fact, some developers are already looking for ways to include it in their projects, such as TrollStore developer @opa334 who could use it to improve TrollNonce. But it’s worth noting that TrollStore will never support anything newer than the firmware it already supports:
Are you excited to see what will become of the new exploit chain? Let us know in the comments section below.
Leave a Reply