How to use Gstatic? All you need to know

If you are browsing the web, you may have seen the gstatic.com website. What is Gstatic.com? Is it a website? Or Virus? It is safe? Will it damage your computer if you use it? How to use it? Will it need to be removed from the computer?
Many netizens are unaware of gstatic.com and perceive it as a virus or malware. So what is gstatic.com? This could be Google’s static code page, designed to produce an HTTP 204 with a “No Content”response.
Loading website content using gstatic.com is fine. Somewhere it is being used by cybercriminals to promote malware and scams. If you frequently encounter a pop-up window that opens from gstatic.com, your computer may be infected with adware.
These ads are usually annoying and redirect you to untrustworthy sites. They even run scripts that download and install unwanted applications.
In this article, we will explain what is gstatic and what does it do? And also destroy the myths associated with it.

What is Gstatic/Gstatic.com and what is it for?
Gstatic or gstatic.com is a domain owned by Google. It plays an important role in helping Google content load faster from their content delivery network (CDN). It also performs the following functions:
- Reduces bandwidth usage
- Speed up Google services like Gmail and Google Maps.
- Improve network performance
- Store static data like JS libraries, stylesheets, etc.
- Verified internet connection (for Android and Chrome)
In addition, it has the following subdomains:
- fonts.gstatic.com: Requests to the Google Fonts API are directed to resource-related domains.
- Maps.gstatic.com: Allows you to embed a Google map image on a web page without using JavaScript.
- csi.gstatic.com: Its main purpose is to improve the performance of other sites.
There is also a fake version of this domain that many cybercriminals use to install unwanted applications. They do not disclose information about the applications associated with them. Therefore, experts advise installing third-party applications only from reliable sources.
Is Gstatic a virus/tracker/safe?
Gstatic is a legitimate Google service that increases bandwidth usage. It also improves network performance.
Examples of its use for bad actions have also been reported. So when you see unwanted pop-ups from gstatic, scan for viruses and malware.
Gstatic is also a tracker. In addition, he needs help to add value to your business. Since 2017, it has become 20-25% less effective than you think.
As we know, Google is a tech giant that is used by billions of people. The proportion of gstatic tracking is increasing every month. No need to worry because it is only used to deliver content and not to track your personal information.
Can you remove Gstatic?
Many people want to remove gstatic because they think it causes issues such as annoying pop-ups and errors.
But gstatic cannot be discounted as it speeds up content delivery.
How did adware get installed on my computer?
Let’s highlight “what is adware”first. This is known as ad-supported software. It automatically generates revenue for its developers by generating adware on your screen. It’s made for computers, but it can also be found on mobile devices. Sometimes he is manipulative and can open the door for suspicious people.
The adware creates an annoying popup that appears on your screen. It can end up on the user’s device in one or two ways.
- You may have installed a free application or computer program without knowing that it contains adware. This will allow the developer to earn money, but means you can download adware without the need for consent.
- There may be a vulnerability on your system that hackers take advantage of with malware, including some adware for your system.
Adware mostly comes with applications or programs that you download from the internet. It will be secretly installed on your device without your knowledge. Advertisements for free software can be annoying, but not illegal. But if a third party adds malicious adware without your consent, it’s illegal.
The adware works silently by installing itself on your device because it is possible that you will accidentally click on the ad that is shown to you. Because the purpose of his existence is to make money.
Adware creators and vendors make money from:
- Pay Per Click: They get paid every time you click on their ad.
- Pay Per View: These will be paid every time you see an ad.
- Installation Fee: They get paid every time the bundled software is installed.
Adware may track your search and browsing history to show you relevant ads. Once they have your location and browsing history, they can earn additional income by selling this information to a third party.
The less harmful part is that the adware just gets in the way. But the more dangerous part is that it could be malicious malware that threatens your cyber security.
How to avoid installing potentially unwanted applications?
Use trusted and authentic resources to download or install applications. Avoid third party software, downloaders, torrent clients, etc.
Also, check custom, advanced, and other options when installing any software. Do not select the optional included unwanted software, then complete the installation.
Many intrusive ads redirect users to untrustworthy websites. Websites are usually about gambling, adult dating or pornography. If you encounter these redirects, check your installed apps and add-ons. Also plug-ins for your browser and remove unnecessary applications immediately.
If your system is already infected with these unwanted applications, we recommend running a scan with a combination antivirus for Windows.
Some gstatic URLs used by Google:
- ssl.gstatic.com
- www.gstatic.comEncrypted.tbn0.gstatic. com
- Encrypted.tbn1.gstatic. com
- Encrypted.tbn2.gstatic. com
- csi.gstatic.com
Adware removal
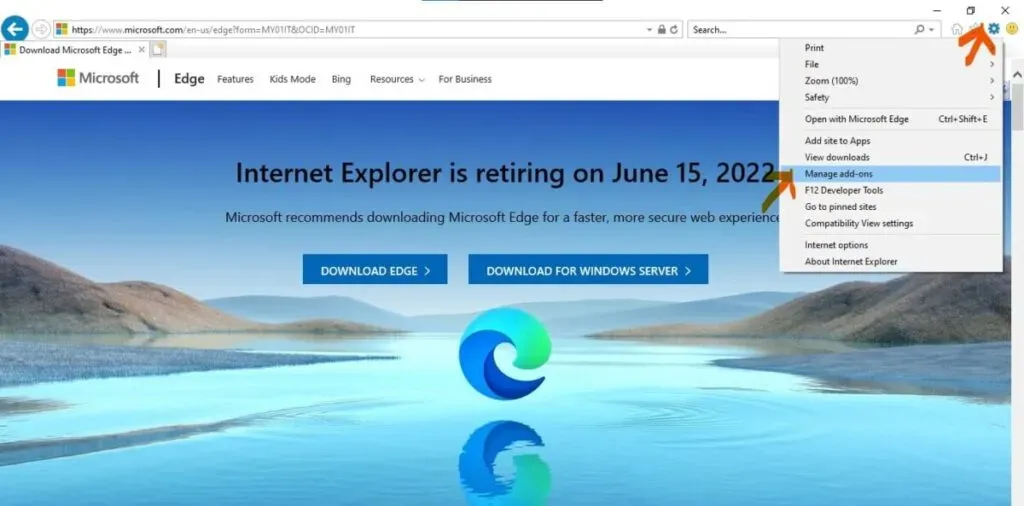
Remove malicious add-ons from Internet Explorer:
- Select the gear icon in the top right corner of the web.
- Select manage add-ons
- Look for any suspicious browser extensions
- Select all and delete.
If you still have problem with gstatic malware removal, reset internet settings to default.
For Windows XP users:
- Choose start
- Click run
- In the window that opens, enter
inetcpl.cpl - In the window that opens, click on the “Advanced”tab.
- Press reset
For Windows Vista and Windows 7 users:
- Click on the Windows logo
- In the initial search field, enter
inetcpl.cpl - Press Enter
- In the window that opens, go to the “Advanced”tab.
- Then hit reset
For Windows 8 users:
- Open Internet Explorer
- Go to gear icon
- Open internet options
- In the window, go to the “Advanced”tab.
- Press the reset button
- Confirm that you want to reset Internet Explorer settings to default by clicking the reset button
Remove adware from internet browsers
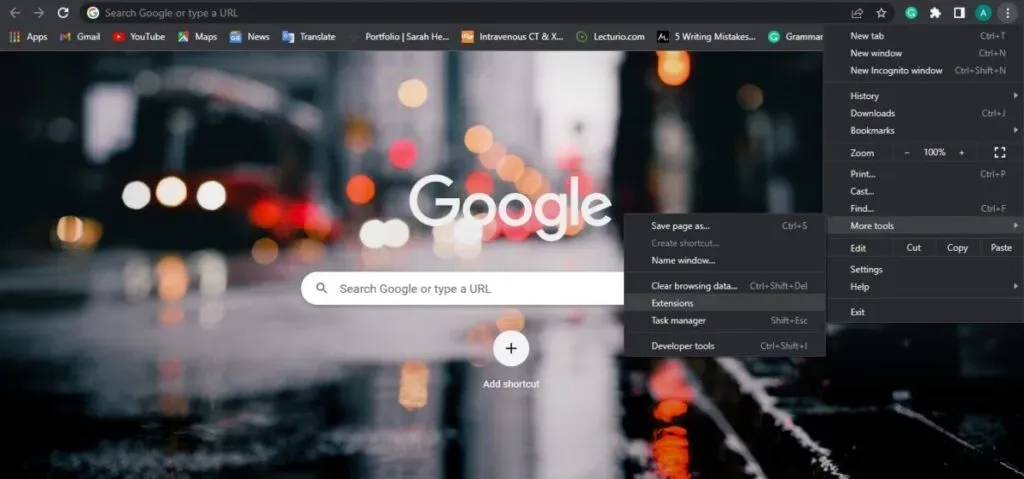
Remove the malicious extension from Google Chrome:
- Click the Chrome menu icon in the top right corner of the screen.
- Navigate to More Tools and click Extensions.
- Look for any recently installed suspicious browser add-ons
- Delete them all
If the problem persists, reset your browser settings.
- Go to Chrome menu icon
- Click Settings
- Scroll down the screen
- Choose extended link
- Press the reset button after scrolling down the screen to restore the default settings.
- Now confirm that you want to reset all settings to default and then click the reset button.
Remove malicious plugins from Mozilla Firefox:
- Click the Firefox menu in the right corner of the screen.
- Click Additions
- Select the extension in the opened window
- Remove any recently installed suspicious browser plugins.
If you are still having trouble removing gstatic malware, try resetting Mozilla Firefox.
- Open the Mozilla Firefox menu in the right corner of the screen.
- Click help in the menu that opens
- Go to Troubleshooting Information
- Click the Firefox update button in the window that opens.
- In the window that opens, make sure you want to reset all Firefox settings to default.
- Then click “Update Firefox Buy Menu”.
Remove malicious extension from Safari
Make sure your Safari browser is active.
- Select the Safari menu and click Preferences.
- In the window that opens, click Extensions
- Select all recently installed suspicious extensions
- Select them all and click Remove.
Another option is to activate the Safari browser:
- Click on the Safari menu
- Scroll down and select clear history and website data
- In the window that opens, select the entire story
- Click the clear history button
Remove the malicious extension from Microsoft Edge:
- Click the edge menu icon in the upper right corner of the screen.
- Select Extensions
- Look for all recently installed suspicious add-ons click
- Select delete under your name
If the gstatic malware removal issue persists, then:
- Go to side menu icon
- Select settings
- In the menu that opens, go to reset settings
- Click restore settings to default.
- In the window that opens, make sure you want to reset Microsoft Edge to default settings.
- Then hit reset
If all these hacks don’t work for you, there are alternatives to make changes to internet browsers. Let’s take a quick look at them:
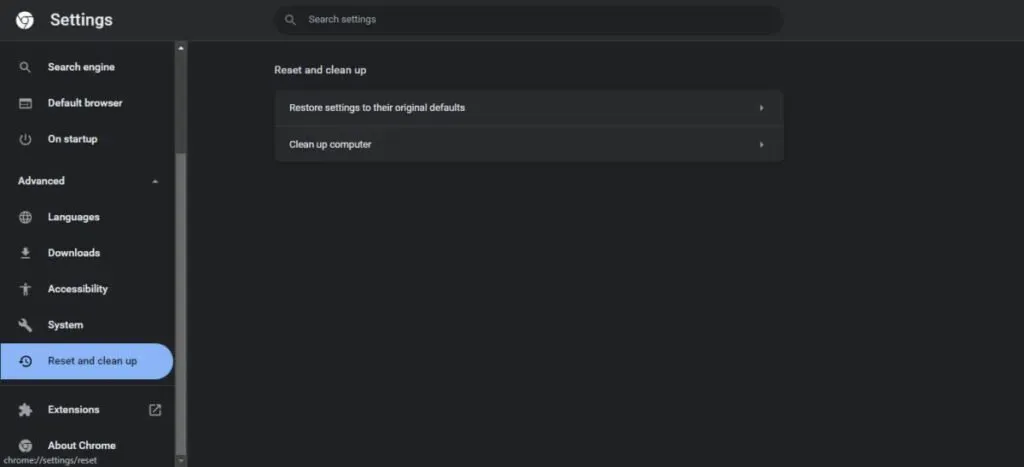
Reset your Google Chrome settings to default:
Resetting Google Chrome will not remove bookmarks and passwords. By resetting Chrome, you can revert to unwanted changes made by adware. Carefully follow the steps below to get your default search engine. Or the home page, default launch tabs, and extensions.
- Go to Google Chrome
- Open the dropdown at the top right corner of the screen and click Settings.
- Scroll down the page and select more
- Scroll down again and restore the original default settings.
- In the confirmation dialog, click Reset.
Reset Mozilla Firefox settings to default:
Resetting Firefox will bring it back to factory settings. The recent feature can fix various issues related to hijackers and adware.
Resetting Firefox will save your important information and open tabs. Follow the instructions to reset the extension. Or themes, search engine, plugin customization, toolbar customization, custom styling, etc.
- Open Firefox
- Press the menu button and select help
- Select Troubleshooting Information
- Select Refresh Firefox
- In the confirmation dialog, click Update Firefox.
- Select Done to complete the process.
Reset Apple Safari to Default
You can remove browser hijackers, adware, and unwanted apps by resetting Apple Safari. Carefully follow the instructions below to reset your browsing history.
Or uninstall extensions, change your homepage, and delete website data. Prior to version 8, Safari had a reset menu item that could be accessed by clicking on Safari and selecting reset.
Those with Safari 8 can reset their browser by doing the following:
- Open apple safari
- Open the Safari menu and select Clear History.
- Scroll down, select all history, then select “Clear History”to complete the process.
- Select the Safari menu and click Preferences.
- Then go to the privacy tab and select manage website data.
- Select delete all
- Select Delete Now to complete the process.
- Click Finish as all website data has been removed.
- Go to the Safari menu and select Preferences
- Select the “Advanced”tab
- Click “Show Develop Menu”in the menu bar.
- Now in the safari menu bar, select Develop and click on Clear Caches.
- Go back to the Safari menu and select Preferences
- Go to the extensions tab, select the extension to remove
- Click Show in Finder
- Right-click the extension, select Move to Trash, or drag it to Trash.
- Enter your password and select OK
Reset your Microsoft Edge settings to default.
Microsoft Edge has become an integral part of Windows. It went through some changes until it was originally released.
Now it’s easy to reset the default settings. The following steps will guide you through factory reset and advanced file deletion method.
You can clear your browsing history, saved website data, cookies, cached data and files, and generate data and passwords by following these steps:
- Open Microsoft Edge
- In the upper right corner, click the ellipsis and click settings
- On the left, select factory reset
- Select restore settings to default.
- In the information dialog, click reset
Final words
Gstatic is a vast topic that is difficult to cover in an article. But in this article, we have tried to help you as much as possible to know what gstatic is, and if it is harmful to your device, then how? If not, what is the real purpose of gstatic.
This will help you improve the performance of your internet connection. If you want to remove it because you think it causes annoying pop-ups and errors, you can’t because it increases content delivery.
This article will also provide you with help regarding adware. What it is, how it can be installed on your device without your knowledge, and how to remove it from different internet browsers.
FAQ
How to disable Gstatic?
You cannot remove gstatic from your device, but you can control adware and suspicious content on your device. If you find any threat or malware in unwanted apps, you should uninstall or uninstall them immediately to protect your device.
Why does Gstatic keep popping up?
If you frequently encounter pop-ups when opening gstatic.com, there is a chance that your device may be infected with adware or other malicious content. Unwanted adware is usually delivered by adware-type software. Or sometimes hijackers are installed without notifying the user.
What is WWW.Gstatic.Com Generate_204?
In many cases, people have been browsing their Internet, they have a problem, and they encounter an error. By clicking on it, they found www.gstatic.com generate_204. The issue only occurred in Chrome and Edge, not Firefox or E11. And later this issue was resolved by obtaining a self-signed certificate.
What is gstatic used for?
This is a Google-owned domain used to download content from a content delivery network (CDN). The CDN is used to download content from a website, which is later accessed via the gstatic domain. Gstatic is also used to store static data. In addition, connection.gstatic.com is another domain used to test Internet connectivity.
Leave a Reply