Google Pixel bug allows you to “unpack” screenshots from the last four years

Back in 2018, Pixel phones got a built-in screenshot editor called Markup with the release of Android 9.0 Pie. The tool appears whenever you take a screenshot, and tapping the app’s pen icon gives you access to tools like cropping and a number of colored drawing pens. This is very handy assuming that the Google Markup tool does indeed do what it says, but the new vulnerability indicates that the changes made by this tool were not in fact destructive! Pixel screenshots taken within the last four years can be cut or unedited.
The bug was discovered by Simon Aarons and named “Acropalypse”or, more formally, CVE-2023-21036. There is an experimental app on acropalypse.app that can undo editing Pixel screenshots, and it actually works! Herethere is also a good technical article by Aaron’s collaborator David Buchanan. The main gist of the problem is that Google’s screenshot editor overwrites the original screenshot file with your new edited screenshot, but it doesn’t truncate or compress that file in any way. If your edited screenshot has a smaller file size than the original – very easy to do with the crop tool – you’ll end up with a PNG with a bunch of junk hidden at the end. This junk data consists of the trailing bits of your original screenshot, and in fact this data can be recovered.
It sounds like a bad way to write a screenshot cropping tool, but in Google’s defense, the Android 9 version of the markup tool worked correctly and cropped the overwritten file. However, Android 10 brought a lot of dramatic “Scoped Storage”changes to how file storage worked in Android. It’s not clear how or why this happened, but perhaps as part of this huge wave of file handling commits, one undocumented change made its way into the Android Framework’s file parser: the framework’s “write”mode stopped truncating overwritten files, and a bug was created in markup. The markup tool relied on OS file handling, and the way it worked changed in a later release that no one seemed to notice.
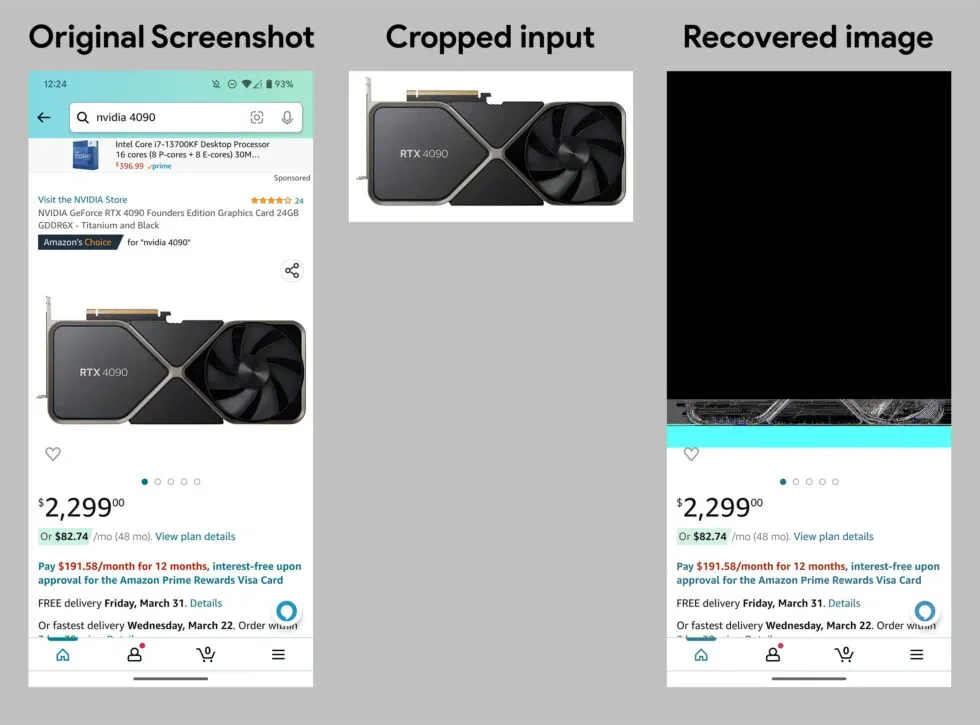
The proof of concept tool on acropalypse.app works great. If you happen to have an uncorrected Pixel device lying around, you can crop the screenshot, feed it into the tool, and you’ll get back the uncropped data. It’s not perfect – you usually end up with a badly corrupted PNG with a big empty area, then a band of fancy colors, but you can pretty reliably restore the bottom of the cropped image. The bug has been fixedin the March 2023 Pixel security update, where it was flagged as a high security vulnerability. This has only ever affected the Pixel screenshot editor, which saves PNGs by overwriting them, and not the Google Photos editor, which saves JPGs by making a new copy. So it’s usually cropped screenshots that are vulnerable, not cropped camera photos, unless you’re doing something really weird like taking a screenshot of your camera output.
However, simply fixing the bug for future users does not really solve the problem. There is still a question about Pixel screenshots from the last four years that are available and possibly full of hidden data that people didn’t realize they were sharing. If you share this screenshot publicly, whether or not the screenshot is a data breach depends on who is posting it. Some apps, such as Twitter, will re-compress any uploaded files, which will remove hidden data from your screenshot. If the app shares the original file instead, the third party may uncrop your screenshot. In particular, Discord has been confirmed to do this, and many other messaging apps are likely using the source file as well.
Leave a Reply